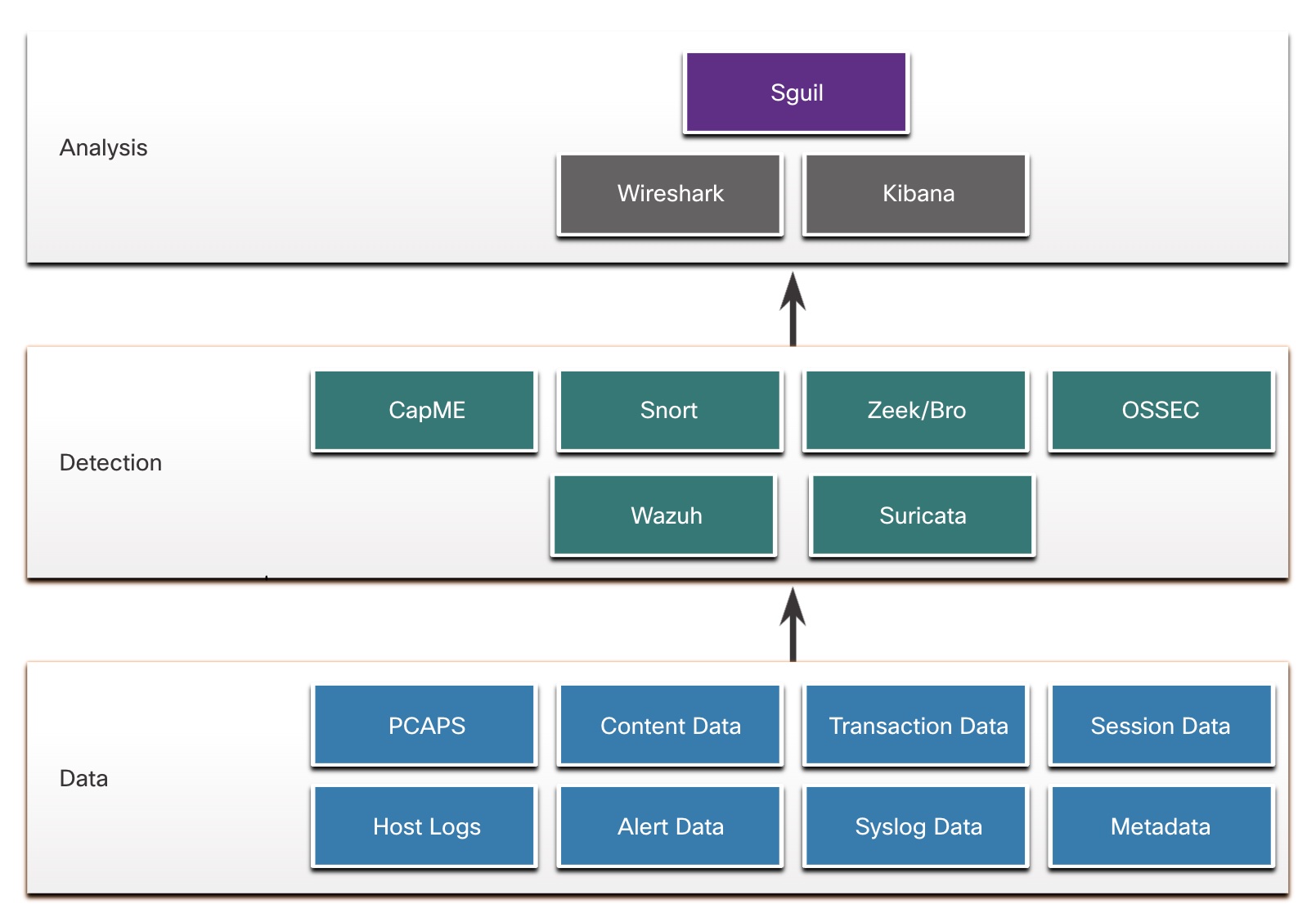
CapMe :This is a web application that allows viewing of pcap transcripts rendered with the tcpflow or Zeek tools. CapME can be accessed from the Enterprise Log Search and Archive (ELSA) tool. CapME provides the cybersecurity analyst with an easy-to-read means of viewing an entire Layer 4 session. CapME acts as a plugin to ELSA and provides access to relevant pcap files that can be opened in Wireshark.
Snort : This is a Network Intrusion Detection System (NIDS). It is an important source of alert data that is indexed in the Sguil analysis tool. Snort uses rules and signatures to generate alerts. Snort can automatically download new rules using the PulledPork component of Security Onion. Snort and PulledPork are open source tools that are sponsored by Cisco.
Zeek : Formerly known as Bro. This is a NIDS that uses more of a behavior-based approach to intrusion detection. Rather than using signatures or rules, Zeek uses policies, in the form of scripts that determine what data to log and when to issue alert notifications. Zeek can also submit file attachments for malware analysis, block access to malicious locations, and shut down a computer that appears to be violating security policies.
OSSEC : This is a host-based intrusion detection system (HIDS) that is integrated into Security Onion. It actively monitors host system operations, including conducting file integrity monitoring, local log monitoring, system process monitoring, and rootkit detection. OSSEC alerts and log data are available to Sguil and Kibana. OSSEC requires an agent to be running on the Windows computers in the enterprise.
Wazuh : is a HIDS that will replace OSSEC in Security Onion. It is a full-featured solution that provides a broad spectrum of endpoint protection mechanisms including host logfile analysis, file integrity monitoring, vulnerability detection, configuration assessment, and incident response. Like OSSEC, it requires agents to be running on network hosts.
Suricata : This is a NIDS that uses a signature-based approach. It can also be used for inline intrusion prevention. It is similar to Zeek; however, Suricata uses native multithreading, which allows the distribution of packet stream processing across multiple processor cores. It also includes some additional features such as reputation-based blocking and support for Graphics Processing Unit (GPU) multithreading for performance improvement.
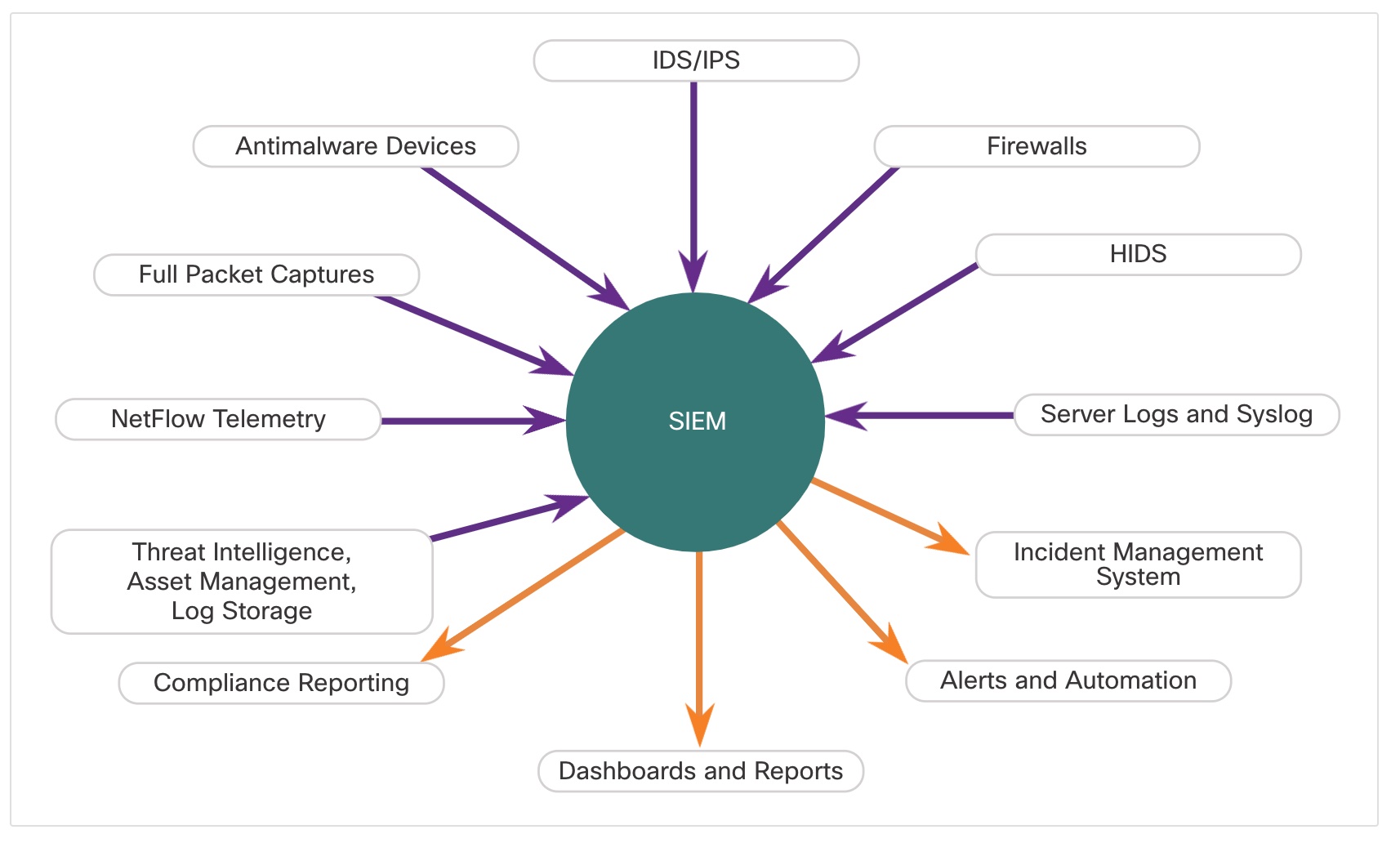
- Sguil – This provides a high-level console for investigating security alerts from a wide variety of sources. Sguil serves as a starting point in the investigation of security alerts. A wide variety of data sources are available to the cybersecurity analyst by pivoting directly from Sguil to other tools.
- Kibana – Kibana is an interactive dashboard interface to Elasticsearch data. It allows querying of NSM data and provides flexible visualizations of that data. It provides data exploration and machine learning data analysis features. It is possible to pivot from Sguil directly into Kibana to see contextualized displays based on the source and destination IP addresses that are associated with an alert. Search the internet and visit the elastic.co website to learn more about the many features of Kibana.
- Wireshark – This is a packet capture application that is integrated into the Security Onion suite. It can be opened directly from other tools and will display full packet captures relevant to an analysis.
- Zeek – This is a network traffic analyzer that serves as a security monitor. Zeek inspects all traffic on a network segment and enables in-depth analysis of that data. Pivoting from Sguil into Zeek provides access to very accurate transaction logs, file content, and customized output.
- NIDS – Snort, Zeek, and Suricata
- HIDS – OSSEC, Wazuh
- Asset management and monitoring – Passive Asset Detection System (PADS)
- HTTP, DNS, and TCP transactions – Recorded by Zeek and pcaps
- Syslog messages – Multiple sources
Alerts will generally include five-tuples information
- SrcIP – the source IP address for the event.
- SPort – the source (local) Layer 4 port for the event.
- DstIP – the destination IP for the event.
- DPort – the destination Layer 4 port for the event.
- Pr – the IP protocol number for the event.