| Term | Description |
|---|---|
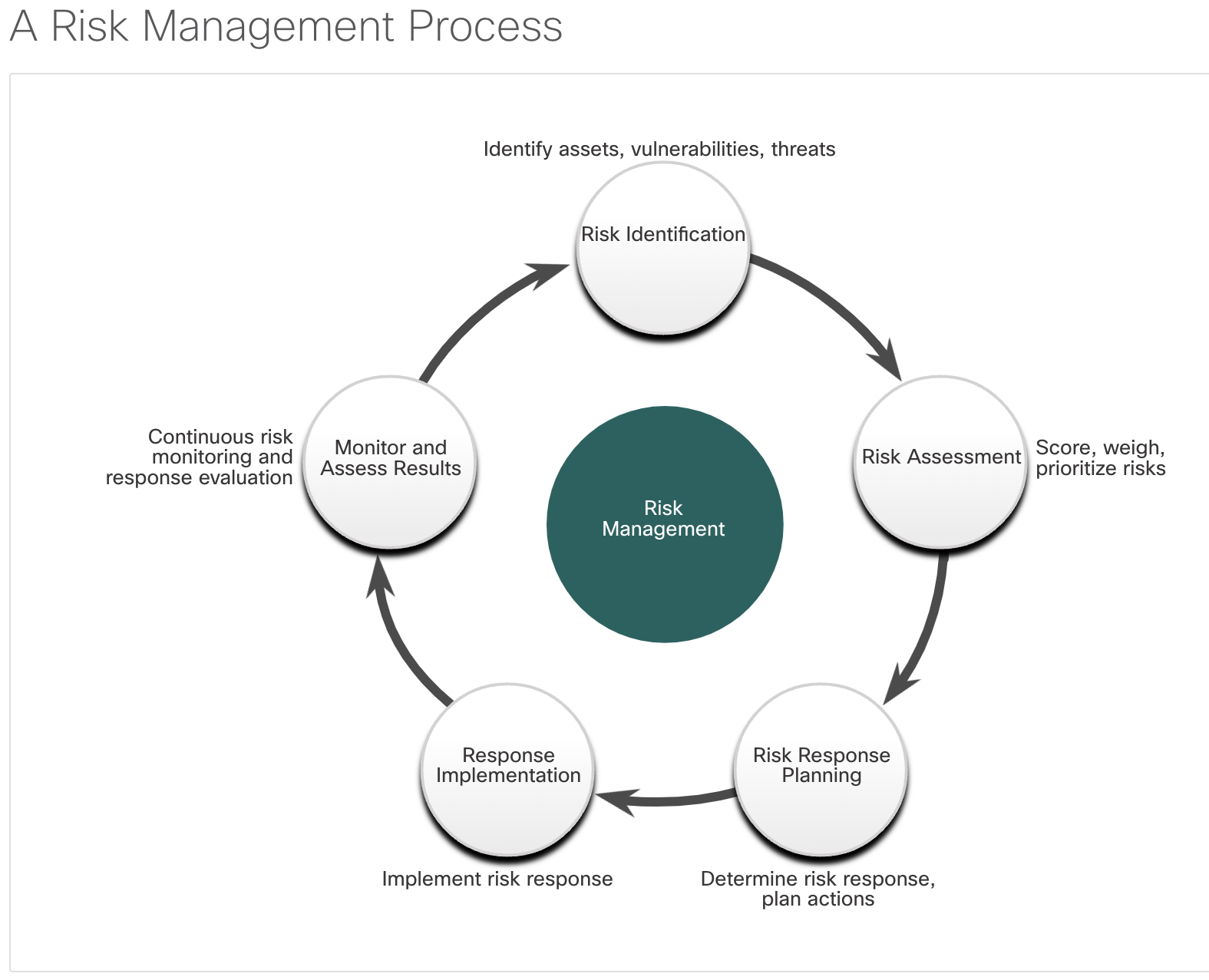
| Risk Analysis |
|
| Vulnerability Assessment |
|
| Penetration Testing |
|
Common Vulnerabilities and Exposures (CVE)
https://www.cvedetails.com/cve/CVE-2005-1943/
National Vulnerability Database (NVD)

I don't know what's the matter with people: they don't learn by understanding, they learn by some other way — by rote or something. Their knowledge is so fragile! (Feynman)
| Term | Description |
|---|---|
| Risk Analysis |
|
| Vulnerability Assessment |
|
| Penetration Testing |
|
Common Vulnerabilities and Exposures (CVE)
https://www.cvedetails.com/cve/CVE-2005-1943/
National Vulnerability Database (NVD)


HIDS Examples are Cisco AMP, AlienVault USM, Tripwire, and Open Source HIDS SECurity (OSSEC).
The Spamhaus Project is an example of a free block list service.
Cuckoo Sandbox is a popular free malware analysis system sandbox.
Other online public sandboxes services are VirusTotal, Joe Sandbox, ANY.RUN, and CrowdStrike Falcon Sandbox.
ApateDNS analyze DNS query request from a host.
ProcMonitor, ProcExp64, RegShot catch event on a PC
Examples of popular web proxies are Squid, CCProxy, Apache Traffic Server, and WinGate.
Cisco’s line of NextGen Firewall devices (NGFW) use Firepower Services to consolidate multiple security layers into a single platform
Public Key (Encrypt) + Private Key (Decrypt) = Confidentiality
Private Key (Encrypt) + Public Key (Decrypt) = Authentication
Hash Operation = Integrity
QuickHash software
Some examples of Certificate Authorities are IdenTrust, DigiCert, Sectigo, GlobalSign, and GoDaddy. These CAs charge for their services. Let’s Encrypt is a non-profit CA that offers certificates free of charge.
A comprehensive security policy has a number of benefits, including the following:
Security policies are used to inform users, staff, and managers of an organization’s requirements for protecting technology and information assets. A security policy also specifies the mechanisms that are needed to meet security requirements and provides a baseline from which to acquire, configure, and audit computer systems and networks for compliance.
The table lists policies that may be included in a security policy.
| Policy | Description |
|---|---|
| Identification and authentication policy | Specifies authorized persons that can have access to network resources and identity verification procedures. |
| Password policies | Ensures passwords meet minimum requirements and are changed regularly. |
| Acceptable Use Policy (AUP) | Identifies network applications and uses that are acceptable to the organization. It may also identify ramifications if this policy is violated. |
| Remote access policy | Identifies how remote users can access a network and what is accessible via remote connectivity. |
| Network maintenance policy | Specifies network device operating systems and end user application update procedures. |
| Incident handling procedures | Describes how security incidents are handled. |
One of the most common security policy components is an AUP.
A BYOD (Bring Your Own Device) security policy should be developed to accomplish the following:
The table lists BYOD security best practices to help mitigate BYOD vulnerabilities.
| Best Practice | Description |
|---|---|
| Password protected access | Use unique passwords for each device and account. |
| Manually control wireless connectivity | Turn off Wi-Fi and Bluetooth connectivity when not in use. Connect only to trusted networks. |
| Keep updated | Always keep the device OS and other software updated. Updated software often contains security patches to mitigate against the latest threats or exploits. |
| Back up data | Enable backup of the device in case it is lost or stolen. |
| Enable “Find my Device” | Subscribe to a device locator service with remote wipe feature. |
| Provide antivirus software | Provide antivirus software for approved BYOD devices. |
| Use Mobile Device Management (MDM) software | MDM software enables IT teams to implement security settings and software configurations on all devices that connect to company networks. |
The table lists various types of access control methods.
| Access Control Models | Description |
|---|---|
| Discretionary access control (DAC) |
|
| Mandatory access control (MAC) |
|
| Role-based access control (RBAC) |
|
| Attribute-based access control (ABAC) | ABAC allows access based on attributes of the object (resource) to be accessed, the subject (user) accessing the resource, and environmental factors regarding how the object is to be accessed, such as time of day. |
| Rule-based access control (RBAC) |
|
| Time-based access control (TAC) | TAC Allows access to network resources based on time and day. |
| AAA Component | Description |
|---|---|
| Authentication |
|
| Authorization |
|
| Accounting |
|
The table lists the differences between the two protocols.
| TACACS+ | RADIUS | |
|---|---|---|
| Functionality | It separates authentication, authorization, and accounting functions according to the AAA architecture. This allows modularity of the security server implementation. | It combines authentication and authorization but separates accounting, which allows less flexibility in implementation than TACACS+ |
| Standard | Mostly Cisco supported | Open/RFC standard |
| Transport | TCP port 49 | UDP ports 1812 and 1813, or 1645 and 1646 |
| Protocol CHAP | Bidirectional challenge and response as used in Challenge Handshake Authentication Protocol (CHAP) | Unidirectional challenge and response from the RADIUS security server to the RADIUS client |
| Confidentiality | Encrypts the entire body of the packet but leaves a standard TACACS+ header. | Encrypts only the password in the access-request packet from the client to the server. The remainder of the packet is unencrypted, leaving the username, authorized services, and accounting unprotected. |
| Customization | Provides authorization of router commands on a per-user or per-group basis | Has no option to authorize router commands on a per-user or per-group basis |
| Accounting | Limited | Extensive |
| Type of Accounting Information | Description |
|---|---|
| Network Accounting | Network accounting captures information for all Point-to-Point Protocol (PPP) sessions, including packet and byte counts. |
| Connection Accounting | Connection accounting captures information about all outbound connections that are made from the AAA client, such as by SSH. |
| EXEC Accounting | EXEC accounting captures information about user EXEC terminal sessions (user shells) on the network access server, including username, date, start and stop times, and the access server IP address. |
| System Accounting | System accounting captures information about all system-level events (for example, when the system reboots or when accounting is turned on or off). |
| Command Accounting | Command accounting captures information about the EXEC shell commands for a specified privilege level, as well as the date and time each command was executed, and the user who executed it. |
| Resource Accounting | The Cisco implementation of AAA accounting captures “start” and “stop” record support for connections that have passed user authentication. The additional feature of generating “stop” records for connections that fail to authenticate as part of user authentication is also supported. Such records are necessary for users employing accounting records to manage and monitor their networks. |
The table lists a few important network security organizations.
| Organization | Description |
|---|---|
| SANS | SysAdmin, Audit, Network, Security (SANS) Institute resources are largely free upon request and include:
|
| Mitre | The Mitre Corporation maintains a list of common vulnerabilities and exposures (CVE) used by prominent security organizations. |
| FIRST | Forum of Incident Response and Security Teams (FIRST) is a security organization that brings together a variety of computer security incident response teams from government, commercial, and educational organizations to foster cooperation and coordination in information sharing, incident prevention and rapid reaction. |
| SecurityNewsWire | A security news portal that aggregates the latest breaking news pertaining to alerts, exploits, and vulnerabilities. |
| (ISC)2 | International Information Systems Security Certification Consortium (ISC2) provides vendor neutral education products and career services to more than 75,000+ industry professionals in more than 135 countries. |
| CIS | The Center for Internet Security (CIS) is a focal point for cyber threat prevention, protection, response, and recovery for state, local, tribal, and territorial (SLTT) governments through the Multi-State Information Sharing and Analysis Center (MS-ISAC). The MS-ISAC offers 24×7 cyber threat warnings and advisories, vulnerability identification, and mitigation and incident response. |
Cisco Annual Cybersecurity Report and the Mid-Year Cybersecurity Report.
Search the internet to locate and download Cisco Cybersecurity Reports from the Cisco website.
You can also subscribe to receive notifications of new blogs by email. Cisco Talos also offers a series of over 80 podcasts that can be played from the internet or downloaded to your device of choice.
Talos maintains the security incident detection rule sets for the Snort.org, ClamAV, and SpamCop network security tools.
FireEye offers SIEM and SOAR with the Helix Security Platform, which uses behavioral analysis and advanced threat detection and is supported by the FireEye Mandiant worldwide threat intelligence network.
The U.S. Department of Homeland Security (DHS) offers a free service called Automated Indicator Sharing (AIS).
The MITRE Corporation defines unique CVE Identifiers for publicly known information-security vulnerabilities to make it easier to share data.
The Malware Information Sharing Platform (MISP) is an open source platform for sharing indicators of compromise for newly discovered threats.
Understanding network security requires you to understand the following terms: threat, vulnerability, attack surface, exploit, and risk. Risk management is the process that balances the operational costs of providing protective measures with the gains achieved by protecting the asset. Four common ways to manage risk are risk acceptance, risk avoidance, risk reduction, and risk transfer. Hacker is a term used to describe a threat actor. White hat hackers are ethical hackers using their skills for good, ethical, and legal purposes. Grey hat hackers are individuals who commit crimes and do unethical things, but not for personal gain or to cause damage. Black hat hackers are criminals who violate computer and network security for personal gain, or for malicious reasons, such as attacking networks. Threat actors include script kiddies, vulnerability brokers, hacktivists, cybercriminals, and state-sponsored hackers. Many network attacks can be prevented by sharing information about indicators of compromise (IOC). Many governments are promoting cybersecurity. CISA and NCSA are examples of such organizations.
| Categories of Tools | Description |
|---|---|
| password crackers | Passwords are the most vulnerable security threat. Password cracking tools are often referred to as password recovery tools and can be used to crack or recover the password. This is accomplished either by removing the original password, after bypassing the data encryption, or by outright discovery of the password. Password crackers repeatedly make guesses in order to crack the password and access the system. Examples of password cracking tools include John the Ripper, Ophcrack, L0phtCrack, THC Hydra, RainbowCrack, and Medusa. |
| wireless hacking tools | Wireless networks are more susceptible to network security threats. Wireless hacking tools are used to intentionally hack into a wireless network to detect security vulnerabilities. Examples of wireless hacking tools include Aircrack-ng, Kismet, InSSIDer, KisMAC, Firesheep, and NetStumbler. |
| network scanning and hacking tools | Network scanning tools are used to probe network devices, servers, and hosts for open TCP or UDP ports. Examples of scanning tools include Nmap, SuperScan, Angry IP Scanner, and NetScanTools. |
| packet crafting tools | Packet crafting tools are used to probe and test a firewall’s robustness using specially crafted forged packets. Examples of such tools include Hping, Scapy, Socat, Yersinia, Netcat, Nping, and Nemesis. |
| packet sniffers | Packet sniffers tools are used to capture and analyze packets within traditional Ethernet LANs or WLANs. Tools include Wireshark, Tcpdump, Ettercap, Dsniff, EtherApe, Paros, Fiddler, Ratproxy, and SSLstrip. |
| rootkit detectors | A rootkit detector is a directory and file integrity checker used by white hats to detect installed root kits. Example tools include AIDE, Netfilter, and PF: OpenBSD Packet Filter. |
| fuzzers to search vulnerabilities | Fuzzers are tools used by threat actors when attempting to discover a computer system’s security vulnerabilities. Examples of fuzzers include Skipfish, Wapiti, and W3af. |
| forensic tools | White hat hackers use forensic tools to sniff out any trace of evidence existing in a particular computer system. Example of tools include Sleuth Kit, Helix, Maltego, and Encase. |
| debuggers | Debugger tools are used by black hats to reverse engineer binary files when writing exploits. They are also used by white hats when analyzing malware. Debugging tools include GDB, WinDbg, IDA Pro, and Immunity Debugger. |
| hacking operating systems | Hacking operating systems are specially designed operating systems preloaded with tools and technologies optimized for hacking. Examples of specially designed hacking operating systems include Kali Linux, SELinux, Knoppix, Parrot OS, and BackBox Linux. |
| encryption tools | These tools safeguard the contents of an organization’s data when it is stored or transmitted. Encryption tools use algorithm schemes to encode the data to prevent unauthorized access to the data. Examples of these tools include VeraCrypt, CipherShed, Open SSH, OpenSSL, OpenVPN, and Stunnel. |
| vulnerability exploitation tools | These tools identify whether a remote host is vulnerable to a security attack. Examples of vulnerability exploitation tools include Metasploit, Core Impact, Sqlmap, Social Engineer Tool Kit, and Netsparker. |
| vulnerability scanners | These tools scan a network or system to identify open ports. They can also be used to scan for known vulnerabilities and scan VMs, BYOD devices, and client databases. Examples of these tools include Nipper, Securia PSI, Core Impact, Nessus, SAINT, and Open VAS. |
Note: There are many tools available on the internet to create ARP MiTM attacks including dsniff, Cain & Abel, ettercap, Yersinia, and others.