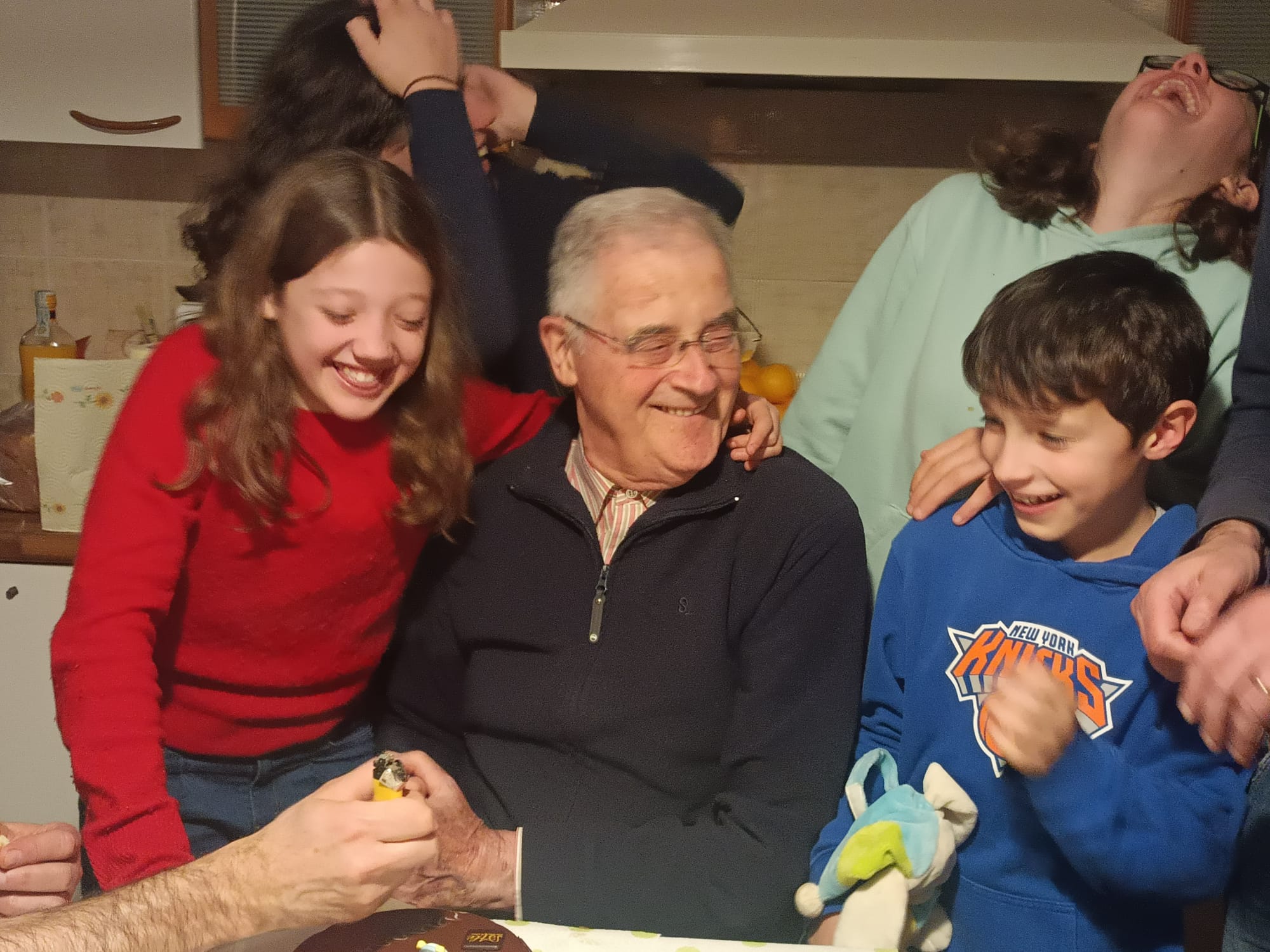Caro Renzo,
A te devo la mia bella famiglia: 36 anni fa convincesti mio marito a venirmi a trovare, nonostante la nebbia fitta e la distanza. Quello stesso anno ci sposammo, e da allora le nostre vite si sono intrecciate in un’amicizia solida, fatta di giornate serene in montagna, passeggiate, pranzi e partite a carte.
Sei stato un esempio di rettitudine e generosità, il Ragioniere con la R maiuscola, sempre onesto, capace e dispensatore di saggi consigli. Hai aiutato tante famiglie senza mai vantartene, seguendo i principi cristiani dell’accoglienza e della condivisione. Così hai fatto, per esempio, con Niaz e Saidul dal Bangladesh e con Giovanni dalla Romania, che hanno saputo costruire una vita nella nostra comunità e ancora oggi ti ricordano con affetto.
Dietro la tua burberità c’era un cuore grande, di chi faceva fatica ad accettare o ignorare le ingiustizie, perché sapevi che l’indifferenza non risolve i problemi. Ricordiamo con un sorriso quando scherzavamo sul fatto che un ragioniere avesse sposato proprio… l’IVA.
Abbiamo fatto di tutto per farti sentire l’affetto dei tuoi amici, dei tuoi figli e dei tuoi nipoti. Eri orgoglioso della tua casa, costruita con sacrificio, e del tuo orto, anche se ogni anno la fatica si faceva sentire di più.
Ci mancherai, caro amico. La tua rettitudine, la tua amicizia e la tua solidarietà cristiana restano il tuo più grande insegnamento.
Buon viaggio, Renzo. Ti abbracciamo forte e, quando arriverai a destinazione, porta il nostro affetto alla cara e indimenticabile Iva.
Pensiero
Con la morte di mio padre mi è stato fatto un regalo. Ho capito che cos’e l’amore e a cosa serve. L’amore non è un sentimento ma un insieme di sentimenti ovvero la sincerità, l’altruismo, la misericordia, la pazienza, la bontà, l’amicizia, la tenerezza, la gentilezza, la giustizia, l’uguaglianza, la solidarietà, la fratellanza, la concordia, la serenità, il dono, la libertà, la vita e la natura. È come un fiore meraviglioso, i cui petali sono fatti di questi sentimenti. L’amore genera ricchezza e benessere per tutti. I popoli e gli Stati che fonderanno le loro politiche sull’amore saranno economicamente e intellettualmente più prosperi. Aver capito questo, aver avuto la possibilità di comprendere cosa mi fa stare bene, è il dono più bello che i miei genitori potessero farmi. Porterò con me per sempre la consapevolezza che l’amore è l’energia che genera la vita.