As cyber threats continue to evolve, security professionals require reliable tools to defend against security vulnerabilities, protect sensitive data, and maintain network security. Open source cyber security tools provide a cost-effective solution for individuals and organizations to combat these threats on-premises and with cloud security and mobile devices. Let’s consider the top 25 open-source cyber security monitoring tools in 2023 that help ensure continuous network and system performance monitoring.
Table of contents
- What are the Top Cybersecurity Threats Today?
- Benefits of Open-Source CyberSecurity tools
- Top 25 Open Source Cyber Security Monitoring Tools in 2023
- 1. Wireshark: Network Protocol Analyzer
- 2. Snort: Network Intrusion Detection and Prevention System
- 3. OSSEC: Host-Based Intrusion Detection System
- 4. Security Onion: Intrusion Detection and Network Security Monitoring Distribution
- 5. Nmap: Network Scanning and Discovery Tool
- 6. Kismet: Wireless Network Detector, Sniffer, and Intrusion Detection System
- 7. Suricata: High-Performance Network Intrusion Detection and Prevention Engine
- 8. Zeek (formerly Bro): Network Analysis Framework for Security Monitoring
- 9. OpenVAS: Vulnerability Scanning and Management Solution
- 10. ClamAV: Open-Source Antivirus Engine
- 11. Fail2Ban: Log-Parsing Application to Protect Against Brute-Force Attacks
- 12. AlienVault OSSIM: Open-Source Security Information and Event Management Platform
- 13. Cuckoo Sandbox: Automated Malware Analysis System
- 14. Logstash: Log Processing and Management Tool
- 15. pfSense: Open-Source Firewall and Router Distribution
- 16. ModSecurity: Open-Source Web Application Firewall
- 17. AIDE (Advanced Intrusion Detection Environment): File and Directory Integrity Checker
- 18. Graylog: Open-Source Log Management Platform
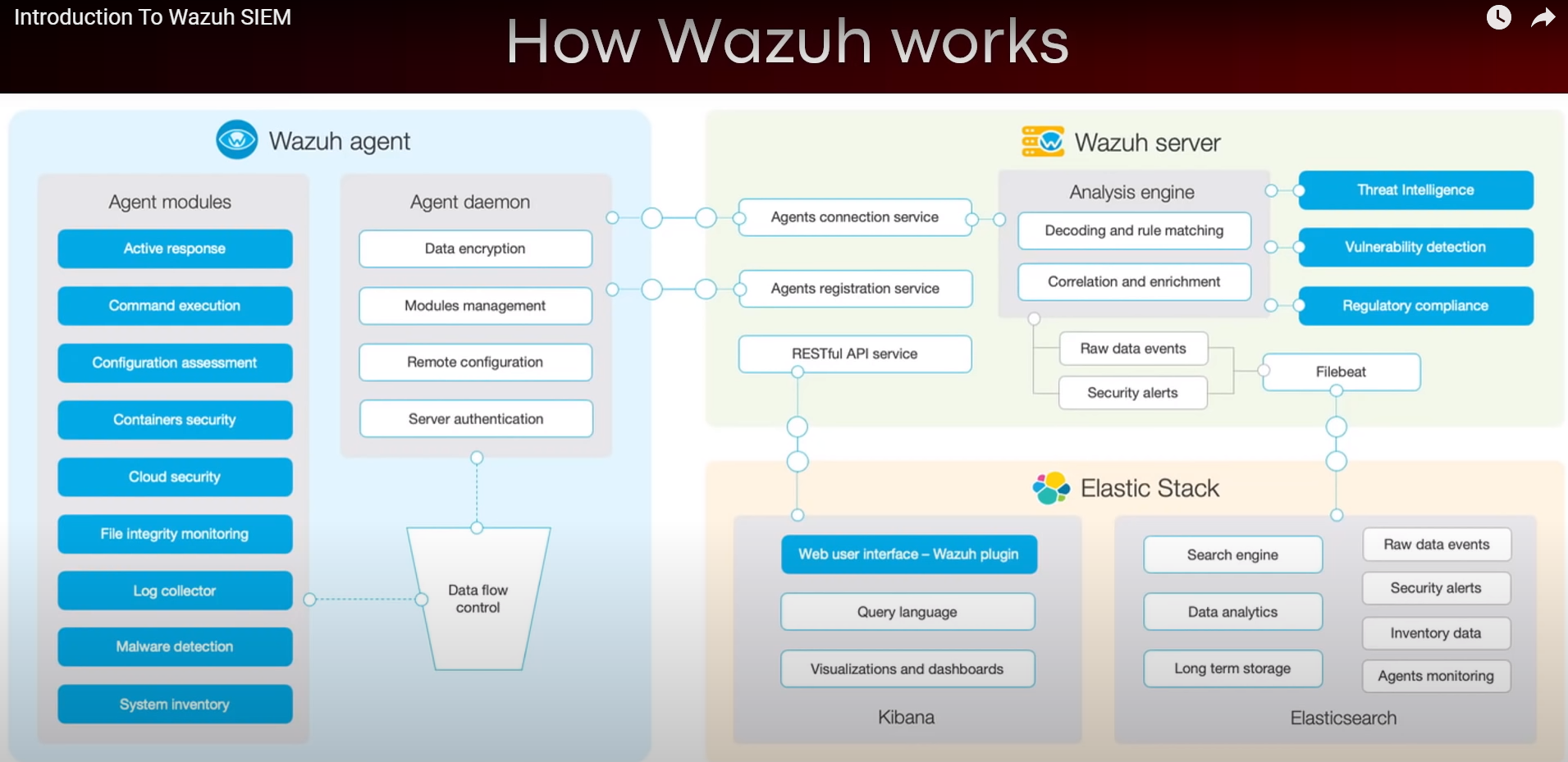
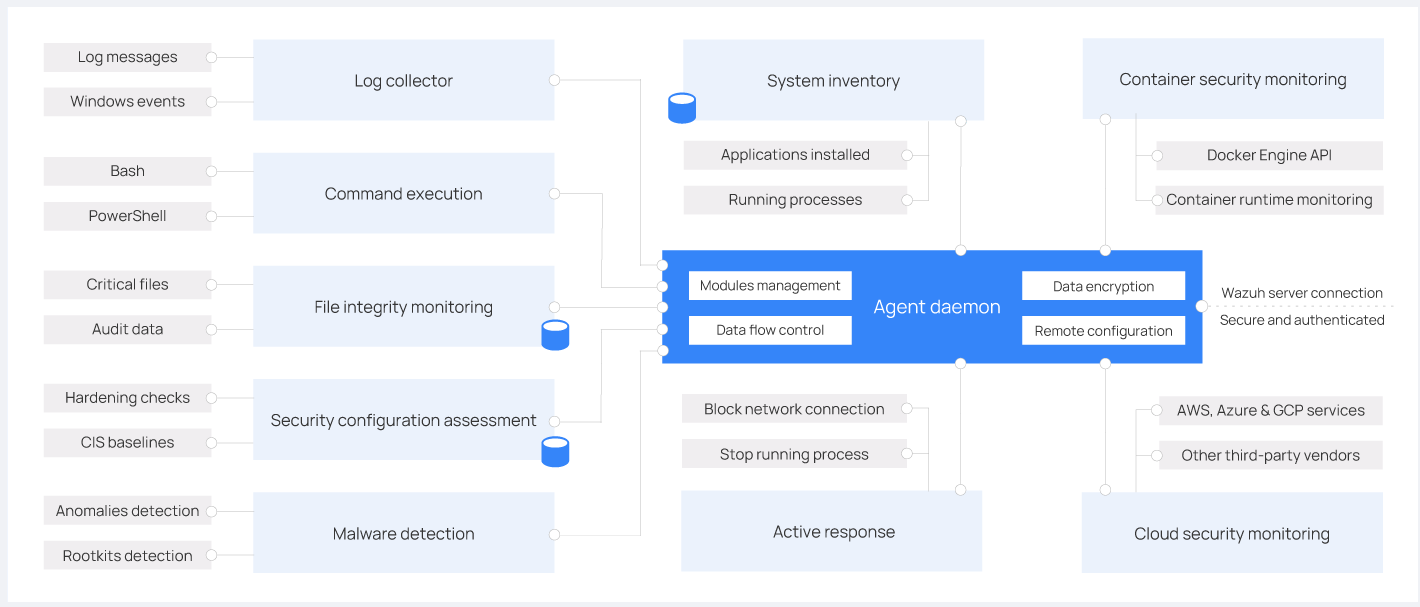
- 19. Wazuh: Security Monitoring and Compliance Solution
- 20. T-Pot: Honeypot Platform
- Honorable mentions
- Tips to Improve Your Cybersecurity Posture
- Frequently Asked Questions (FAQs)
- Wrapping up
- Other posts you may enjoy
What are the Top Cybersecurity Threats Today?
As cyber threats continue to evolve and become more sophisticated, organizations must stay informed and prepared to defend against a wide range of security risks.
Here are the top cybersecurity threats that businesses and individuals should be aware of today:
1. Phishing Attacks: Phishing attacks are a prevalent form of social engineering where cybercriminals use deceptive emails or websites to trick users into revealing sensitive information or installing malware. These attacks often target login credentials, financial information, and other personal data.
2. Ransomware: Ransomware is a type of malicious software that encrypts a victim’s files or locks their systems, demanding a ransom payment to restore access. Ransomware attacks can cause significant financial losses and operational disruptions for organizations.
3. Insider Threats: Insider threats refer to security risks posed by employees, contractors, or other individuals with authorized access to an organization’s systems and data. These threats can result from malicious intent or negligence, leading to data breaches or system compromises.
4. Supply Chain Attacks: Also known as third-party attacks or vendor risk, supply chain attacks target an organization’s suppliers, vendors, or partners to gain access to their systems and data. These attacks often exploit security vulnerabilities in the supply chain to compromise multiple organizations.
5. Distributed Denial of Service (DDoS) Attacks: DDoS attacks involve overwhelming a target’s network or system with a flood of traffic, rendering it inaccessible to legitimate users. DDoS attacks can cause severe downtime and service disruptions.
6. Advanced Persistent Threats (APTs): APTs are sophisticated, coordinated cyberattacks by well-funded threat actors or nation-state groups that target specific organizations for espionage, data theft, or sabotage. APTs often use advanced techniques and tactics to evade detection and maintain a long-term presence within a target’s network.
7. Zero-Day Exploits: Zero-day exploits are attacks that take advantage of previously unknown security vulnerabilities in software or systems. These vulnerabilities, also known as zero-day flaws, have no existing patches or fixes, making them particularly dangerous and challenging to defend against.
8. Internet of Things (IoT) Security: The increasing adoption of IoT devices and connected technologies has expanded the attack surface for cybercriminals. IoT devices are often vulnerable to cyber threats due to weak security measures, creating new risks for organizations and consumers.
9. Data Breaches: Data breaches occur when unauthorized individuals gain access to an organization’s sensitive data, such as customer information, financial records, or intellectual property. Data breaches can result in significant financial and reputational damage for organizations.
10. Cloud Security Threats: As more organizations migrate to cloud-based services, cloud security has become a critical concern. Threats in the cloud can arise from misconfigurations, weak authentication mechanisms, and vulnerabilities in cloud applications or infrastructure.
Benefits of Open-Source CyberSecurity tools
Open source cyber security monitoring tools offer numerous advantages over proprietary solutions, making them an attractive option for businesses, organizations, and individuals looking to enhance their security posture and perform effective security testing.
Here are some key benefits of using open-source tools for cyber security monitoring for monitoring services that pose security threats, even if you have another network monitoring system. Proper cybersecurity monitoring and access management are key to maintaining a secure environment.
Cost-Effectiveness
One of the most significant benefits of open-source cyber security tools is their cost-effectiveness. With no licensing fees or subscription costs, these free tools enable security teams to access powerful network monitoring solutions without breaking the bank.
This particularly benefits small businesses and startups with limited budgets, allowing them to allocate resources to other critical areas.
Customizability and Flexibility
Open-source network monitoring tools offer high customizability and flexibility, allowing security professionals to tailor the tools to their specific needs. This adaptability enables organizations to address unique security threats and vulnerabilities, ensuring a more robust security posture.
Additionally, the ability to integrate these tools with existing security infrastructure adds an extra layer of protection to network security.
Rapid Development and Updates
The open-source community is known for its rapid development and frequent updates. As new security threats and vulnerabilities emerge, open-source cyber security tools are often among the first to receive patches and updates.
This continuous monitoring and proactive response help organizations stay ahead of potential security risks and maintain a strong security posture.
Extensive Support and Collaboration
Open-source cyber security tools benefit from an extensive support network, comprising developers, users, and experts from around the world.
This collaborative environment fosters knowledge sharing, allowing security professionals to learn from one another and develop more effective security strategies.
Additionally, the availability of comprehensive documentation and online forums makes it easier for users to troubleshoot issues and enhance their understanding of network monitoring and security.
Improved Security and Transparency
With their source code openly available for inspection, open-source cyber security tools offer greater transparency than proprietary alternatives. This transparency allows security professionals and researchers to scrutinize the code for potential security vulnerabilities and ensure its integrity.
Moreover, the collaborative nature of the open-source community means that any identified issues are addressed quickly, further enhancing the overall security of these tools.
Platform Independence and Interoperability
Open-source network monitoring software often supports a wide range of operating systems, including Windows, macOS, and Linux, allowing organizations to deploy these tools across diverse environments.
This platform independence and interoperability help organizations ensure comprehensive network monitoring, regardless of the underlying infrastructure.
Top 25 Open Source Cyber Security Monitoring Tools in 2023
Note the following free cyber security monitoring tools in 2023 and the open-source list of solutions you can take advantage of and no free trial needed.