| Term |
Description |
| Risk Analysis |
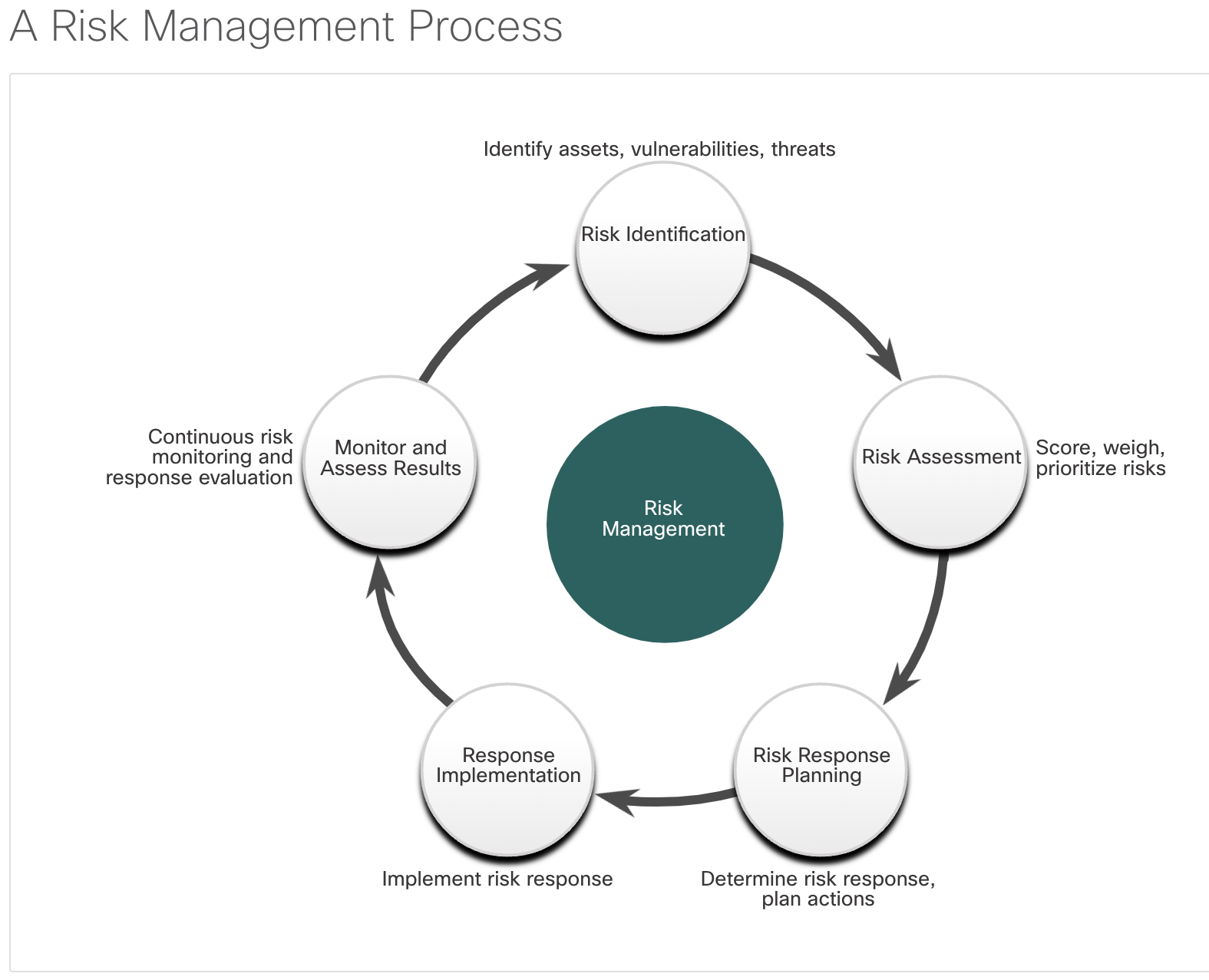
- This is a discipline in which analysts evaluate the risk posed by vulnerabilities to a specific organization.
- A risk analysis includes assessment of the likelihood of attacks, identifies types of likely threat actors, and evaluates the impact of successful exploits on the organization.
|
| Vulnerability Assessment |
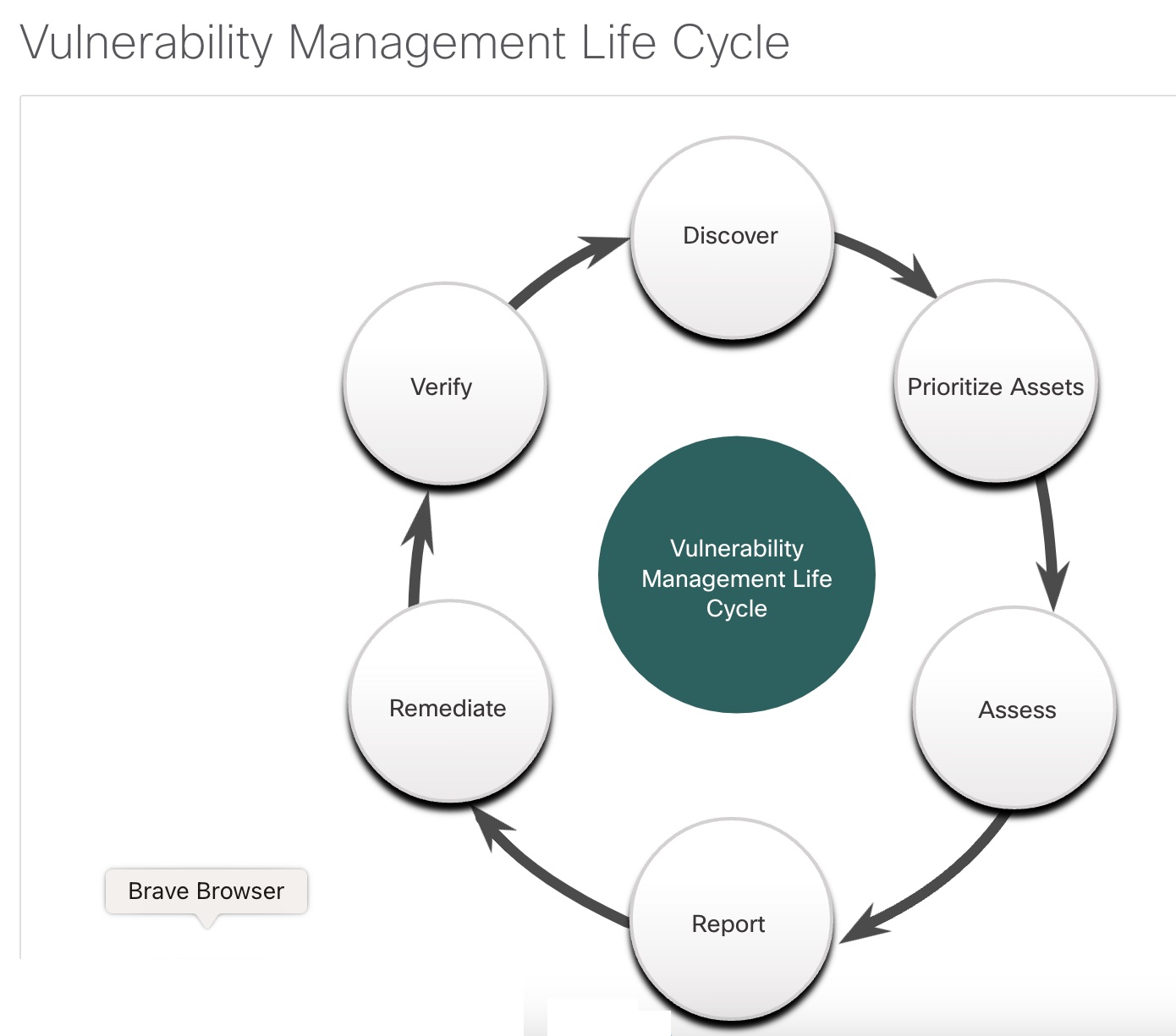
- This test employs software to scan internet facing servers and internal networks for various types of vulnerabilities.
- These vulnerabilities include unknown infections, weaknesses in web-facing database services, missing software patches, unnecessary listening ports, etc.
- Tools for vulnerability assessment include the open source OpenVAS platform, Microsoft Baseline Security Analyzer, Nessus, Qualys, and FireEye Mandiant services.
- Vulnerability assessment includes, but goes beyond, port scanning.
|
| Penetration Testing |
- This type of test uses authorized simulated attacks to test the strength of network security.
- Internal personnel with hacker experience, or professional ethical hackers, identify assets that could be targeted by threat actors.
- A series of exploits is used to test security of those assets.
- Simulated exploit software tools are frequently used.
- Penetration testing does not only verify that vulnerabilities exist, it actually exploits those vulnerabilities to determine the potential impact of a successful exploit.
- An individual penetration test is often known as a pen test.
- Metasploit is a tool used in penetration testing.
- CORE Impact offers penetration testing software and services.
|
Common Vulnerabilities and Exposures (CVE)
cve.mitre.org
https://www.cvedetails.com/cve/CVE-2005-1943/
National Vulnerability Database (NVD)
nvd.NIST.gov